Trickbot, also known as Trickster or TrickLoader, is a notorious Trojan that has been actively targeting Windows systems since 2016. Initially identified as a banking Trojan, Trickbot has evolved into a modular malware capable of a wide range of malicious activities, including data theft, network infiltration, and ransomware deployment. For those concerned about potential Trickbot infections, tools like Farbar Recovery Scan Tool (FRST) can be invaluable in identifying and addressing the malware’s presence.
This article will guide you on how to use Farbar Recovery Scan Tool to detect Trickbot infections and outline the necessary steps to mitigate this threat.
Understanding the Trickbot Trojan
Trickbot emerged in September 2016, discovered by cybersecurity researchers at Malwarebytes Labs. It was initially recognized for its similarities to the Dyre Trojan, a prominent banking malware of the time. Trickbot quickly gained notoriety, becoming one of the most active Trojans, often ranking among the top 10 most prevalent malware threats.
Trickbot’s modular design allows its operators, believed to be the Wizard Spider group from Russia, to customize attacks by deploying specific modules for different targets and objectives. Over time, Trickbot has incorporated at least 29 different techniques, according to Mitre.org, showcasing its versatility and adaptability.
Here’s a brief timeline of Trickbot’s evolution:
September 2016: Genesis of Trickbot
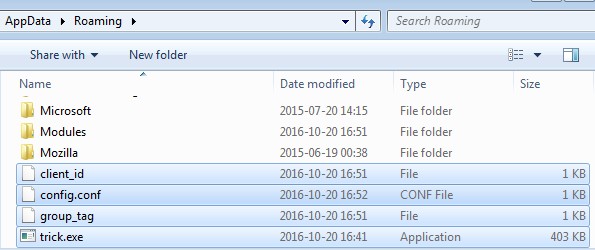
Trickbot was first identified as a new bot resembling the Dyre Trojan. It was named Trickbot based on text found within its code. Infection vectors included malvertising and fake ads containing Rig Exploit Kits (EK). Upon infection, Trickbot would copy itself to the /APPDATA/ folder, naming itself “trick.exe,” and download modules and configuration files from Command and Control (CnC) servers.
Early modules included injectDll32 for browser injection and credential theft, and systeminfo32 for gathering system information. Trickbot also established persistence by adding itself to Windows Task Scheduler. Researchers noted strong similarities to Dyre, suggesting a connection between the developers of both Trojans.
Executable file Trickbot installation
December 2016: Expanding Capabilities – Local Database Theft
A new module, mailsearcher32, enabled Trickbot to scan for and exfiltrate email data. Another module, importDll32, was introduced to steal browser data, including cookies, local storage (Flash SharedObjects, HTML5 local storage, SQLite), and browsing history. This module also incorporated browser fingerprinting techniques, allowing Trickbot to gather browser configurations discreetly.
July 2017: EternalBlue Exploitation
Trickbot’s activity surged in the summer of 2017, targeting financial institutions across Europe, Australia, the United States, and expanding to Latin America. It utilized the Necrus botnet for spam distribution. A significant development was the integration of the wormDll32 module, leveraging the EternalBlue exploit (MS17-010). This allowed Trickbot to spread more effectively within targeted networks, although it appeared to be used cautiously compared to ransomware like WannaCry and NotPetya.
November 2017: Account Takeover (ATO) Attacks
The bcClientDllTest module was introduced for Account Takeover (ATO) attacks. Trickbot would download SOCK5 proxy modules, using the victim’s IP as a proxy to test online accounts. By mimicking mobile logins, Trickbot aimed to bypass traditional anti-fraud detection systems.
March 2018: Screenlocker Experiments
The tabDll32 or spreader_x86.dll module included screenlocker functionality. While seemingly deviating from its banking Trojan roots, this feature was speculated to be aimed at corporate network users less likely to engage in online banking on their work devices. Instead of direct financial theft, locking screens and demanding ransom became an alternative approach. Researchers found that the screen locking was used to force users to re-enter credentials, which Trickbot then stole using tools like Mimikatz.
August 2018: Stealth Techniques
Trickbot adopted stealthier techniques, including Hollow Process Injection to inject malicious code into legitimate Windows processes. This variant also aimed to evade antivirus analysis and disable Windows Defender, similar to the Flokibot Trojan. “Zoom in” macro techniques were used to delay malicious activity in infected MS Word documents, triggering only when users interacted with the zoom feature, executing PowerShell code to download and run Trickbot.
PowerShell code execution triggered by Zoom In action
November 2018: Network Invasion and POS Targeting
A new module, pwgrab32, expanded credential theft capabilities to include passwords from Microsoft Outlook, Filezilla, WinSCP, Chrome, Firefox, Microsoft IE, and Microsoft Edge. Modules like shareDll32, wormDll32, and networkDll32 were used for network propagation and reconnaissance. The psfin32 module indicated a move towards targeting Point of Sale (POS) systems, using LDAP queries to identify POS software and related services on compromised networks.
psfin32 module targeting POS systems
January 2019: Ransomware Partnership
Trickbot was observed being used to deploy Ryuk ransomware. This indicated a business partnership where Trickbot operators would provide initial access to networks, which Ryuk operators would then encrypt for ransom.
February 2019: Remote Application Credentials
Updated pwgrab32 modules targeted credentials for remote applications like VNC, PuTTY, and RDP, enabling remote control of compromised systems.
April 2019: Triple Threat Attacks
“Triple Threat” attacks involving Emotet, Trickbot, and Ryuk emerged. Emotet would initially infect systems, followed by Trickbot for further infiltration and reconnaissance, culminating in Ryuk ransomware deployment.
Triple Threat workflow involving Emotet, Trickbot, and Ryuk
July 2019: Web Injection Techniques
Trickbot adopted web injection code from BokBot (IcedID), enabling man-in-the-browser attacks. This allowed Trickbot to redirect victims to fake banking sites or manipulate content on legitimate banking websites, stealing credentials and financial information.
Web Injection technique used by Trickbot
August 2019: Fileless Operations
Trickbot began employing fileless techniques, particularly on Windows 10 64-bit systems. This made detection more challenging as modules and configurations were no longer stored as physical files on disk.
September 2019: Alternate Data Streams (ADS) Manipulation
Trickbot utilized Alternate Data Streams (ADS) in Windows NTFS to further enhance its stealth. Malicious code was hidden within ADS, making it harder to detect through traditional file system scans. This version also included self-updating capabilities and the ability to download and execute additional malware, storing downloaded files within ADS to evade detection.
How to Use Farbar Recovery Scan Tool (FRST) to Detect Trickbot
Farbar Recovery Scan Tool (FRST) is a powerful diagnostic tool that can help identify malware infections, including Trickbot, on Windows systems. Here’s how to use it:
1. Download FRST:
- Visit the official download page on BleepingComputer: https://www.bleepingcomputer.com/download/farbar-recovery-scan-tool/
- Download the appropriate version for your system (FRST.exe for 32-bit Windows, FRST64.exe for 64-bit Windows).
2. Run FRST:
- Close all running programs and browsers.
- Run FRST as an administrator. Right-click on the downloaded FRST executable and select “Run as administrator.”
- If prompted by User Account Control (UAC), click “Yes” to allow FRST to run.
3. Initiate Scan:
- Once FRST is open, you will see a user interface with several checkboxes and options.
- For a standard Trickbot detection scan, ensure the default checkboxes are selected. These typically include:
- Registry
- Files
- Internet
- Services
- Drivers
- Processes
- Additional Options (often includes things like List BCD, etc.)
- Click the “Scan” button.
4. Wait for the Scan to Complete:
- FRST will begin scanning your system. This process may take several minutes depending on your system’s size and speed.
- Do not interrupt the scan.
5. Review Scan Logs:
- Once the scan is complete, FRST will generate two log files in the same directory where you ran FRST:
FRST.txt: This is the primary scan log containing detailed information about your system’s registry, files, processes, services, and more.Addition.txt: This log contains additional details about system additions and configurations.
- Open both
FRST.txtandAddition.txtusing Notepad or any text editor.
6. Analyze Logs for Trickbot Indicators:
- Review the logs for suspicious entries related to Trickbot. Look for:
- Filenames or paths mentioned in Trickbot’s history (e.g.,
trick.exe, files inAppDataRoamingmsnet, etc.). - Suspicious processes or services that you don’t recognize.
- Unusual registry entries or modifications.
- Entries related to network connections to known malicious IPs or domains.
- Filenames or paths mentioned in Trickbot’s history (e.g.,
- If you are unsure about interpreting the logs, seek assistance from cybersecurity forums or professionals who are experienced in malware analysis. Many online communities can help analyze FRST logs for signs of infection.
Example of Indicators to look for (This is not exhaustive and Trickbot evolves):
- File paths: Entries under
ProcessesorFilessections pointing to locations likeC:Users[Username]AppDataRoamingmsnetor similar suspicious paths. - Service Names: Look for services with generic or misleading names that might be Trickbot’s autostart services (as mentioned in the timeline, like “Service Techno,” “Technoservices,” etc.).
- Registry Keys: Suspicious entries in
Registrysections related to startup or Run keys that point to unusual executables. - Network Activity: While FRST logs don’t directly show real-time network activity, they can list processes and services that might be associated with network connections.
Important Note: FRST is a diagnostic tool. It helps identify potential malware but does not automatically remove infections.
Steps to Take After Detecting a Potential Trickbot Infection
If FRST logs or other indicators suggest a Trickbot infection, take the following steps:
-
Disconnect from the Network: Immediately disconnect your computer from the internet and any local network to prevent further communication with CnC servers and lateral movement within the network.
-
Patch EternalBlue Vulnerability: Ensure that the MS17-010 security update (EternalBlue patch) is installed on your system. Microsoft provides guidance on this: https://support.microsoft.com/en-us/help/4013389/title
-
Disable Administrative Shares: Disable administrative shares to limit Trickbot’s ability to spread within a network.
-
Malware Removal with Antivirus/Antimalware: Use a reputable antivirus or antimalware program to scan your system and remove Trickbot. Ensure your antivirus is updated to the latest definitions. Run a full system scan.
-
Change Passwords: Change passwords for all accounts, especially those that might have been compromised, such as online banking, email, and system login credentials.
By using Farbar Recovery Scan Tool and following these remediation steps, you can effectively detect and address Trickbot infections, safeguarding your system and data from this sophisticated Trojan. Remember to stay vigilant and practice good cybersecurity habits to prevent future infections.
References:
- bleepingcomputer.com
- malwarebytes.com
- f5.com
- securityintelligence.com
- cyberbit.com
- trendmicro.com
- fortinet.com
- cybereason.com